Memory Integrity Enforcement (MIE) is a hardware-level security architecture introduced with the iPhone 17 and iPhone Air using A19 System-on-Chip (SoC) which combines existing memory safety defenses in iOS with ARM’s Memory Tagging Extension (MTE). It is designed to eliminate memory corruption vulnerabilities, the primary tools used by sophisticated spyware like Pegasus.
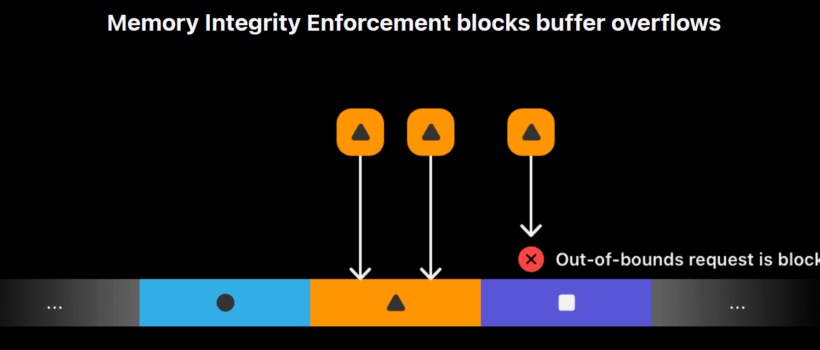
The new hardware security feature is not widely known. MIE works by attaching cryptographic tags to different sections of the device’s memory. When a program attempts to access a piece of memory, the A19 chip verifies that the tag matches. If a mismatch is detected, which could indicate an unauthorized attempt to access or modify data, the chip immediately blocks the operation. This process helps to prevent common attack vectors such as buffer overflows and use-after-free exploits.
Memory Integrity Enforcement checks memory in real-time. If a program tries to access memory with the wrong tag, the A19 chip instantly terminates the process. Apple dedicated significant areas of the A19 and A19 Pro chips specifically to these security checks to ensure there is minimal impact on device performance. Tag Confidentiality Enforcement (TCE) keeps these randomized tag values hidden to prevent “leak” attacks or side-channel exploits like Spectre.
Apple’s improving memory safety has been an ongoing effort, first with the rollout of Swift, a memory-safe language. In iOS 15, Apple introduced a secure memory allocator for the kernel, followed in iOS 17 by its user-level counterpart. These secure allocators take advantage of knowing the type of allocations so that memory can be organized in a way that makes exploiting most memory corruption vulnerabilities inherently difficult. In 2018, Apple released Pointer Authentication Codes (PAC) in the A12 Bionic chip to protect code flow integrity in the presence of memory corruption.
Memory Integrity Enforcement (MIE) is only on A19 and A19 Pro chips, included with the iPhone 17 series and the iPhone Air. It is always on by default for the kernel and core system processes users do not need to enable it. Apple has provided an “Enhanced Security” option in Xcode, so third-party developers can opt-in and test their own apps with EMTE protections.
I know Apple will build this into iPads eventually, and I hope they build this into M-series Macs as well in the future.